Smart devices can help seniors age in place, improve the quality of life for individuals of any age and much more. That being said, there are some drawbacks to smart devices, too.
If someone is able to hack your smart technology, he or she could steal your identity, break into your home and cause serious damage to your life overall.
To take advantage of all that the Internet of Things has to offer in a safe way, you need to understand how you can protect your home and personal smart devices and learn about the most hackable smart devices.
1) A Smart Hub
Would you believe that hacking a smart home isn’t so hard to do?
At a convention earlier this year, Kaspersky Lab showed that hacking smart appliances is pretty simple. If a hacker gains access to your smart hub, which is essentially a piece of technology that “talks” to all the smart devices in your home, they can steal invaluable information from you.
After a criminal discovers the login and password to a smart hub, which isn’t difficult to do, he or she can gain complete access to all the devices it controls. If this invasion of privacy is hard to conceptualize, here’s an example of how it might play out:
You are sound asleep in the middle of the night, and your room is set to the perfect temperature. At some point, you need to use the restroom, so you sit up in your bed.
As your feet swing onto the floor, your overhead lights turn on slightly, so they illuminate your walk to the restroom. After you use the bathroom and crawl back into bed, the lights dim, and a sound machine turns on to help you get back to sleep.
In another situation, you could wake up in the middle of the night to use your restroom, only to find that the lights don’t turn on when you go to stand up.
Next, you find that your room is very cold, and something’s wrong with your thermostat. Instead of hearing your sound machine, you hear your footsteps, only to realize that your TV is playing a real-time video of you from the security camera outside your window.
Unfortunately, the two situations above are realistic examples of what can happen when a smart hub is compromised. Smart hubs are easily hackable, which is why it’s important to do extensive research and talk one-on-one with an adviser from a computer and technical support company before you purchase one for your home.
2) Baby Monitors
When it comes to children, the importance of security and safety can’t be understated.
For many parents, the only way to leave a baby alone in a room is if he or she can be seen and heard. Baby monitoring devices help parents keep track of their little ones and make sure they’re OK. Unfortunately, parents aren’t necessarily always the only ones looking at children with smart devices.
According to experts at the Ben-Gurion University of the Negev in Israel, a simple Google search can allow cybercriminals to hack smart baby monitors. Once hacked, the criminals can see a real-time video feed, play loud music through the monitor and even control the camera remotely.
Consumers often don’t change default security settings, like passwords, when they purchase a smart baby monitor, which is partially why they’re so easily corruptible.
So, if you would like to use one of these devices, make sure you first alter its default settings and implement a hard-to-guess and hard-to-hack password.
It’s also a good practice to buy a new device from a reputable company.
Second-hand baby monitors may save you some money, but they could be infected with malware that could cause you and your child harm.
3) Thermostats
On the back of many smart thermostats, there’s a Universal Serial Bus (USB) port.
These ports are standard connection types for many different devices, like keyboards, flash drives, cameras, printers and more. If someone wants to access the software on a smart thermostat, all her or she needs to do is access its USB.
After he or she has access to a USB, they can alter its software or corrupt it in another way that they see fit. For example, he or she might decide to raise the temperature in a home as high as it’ll go, increasing the chance of an electrical fire.
Similarly to a smart baby monitor, you never want to buy a used smart home thermostat.
The owner before you could put malicious software on the device. Then, when you connect the thermostat to your WiFi, the criminal could gain information about when you’re home, your WiFi password and more.
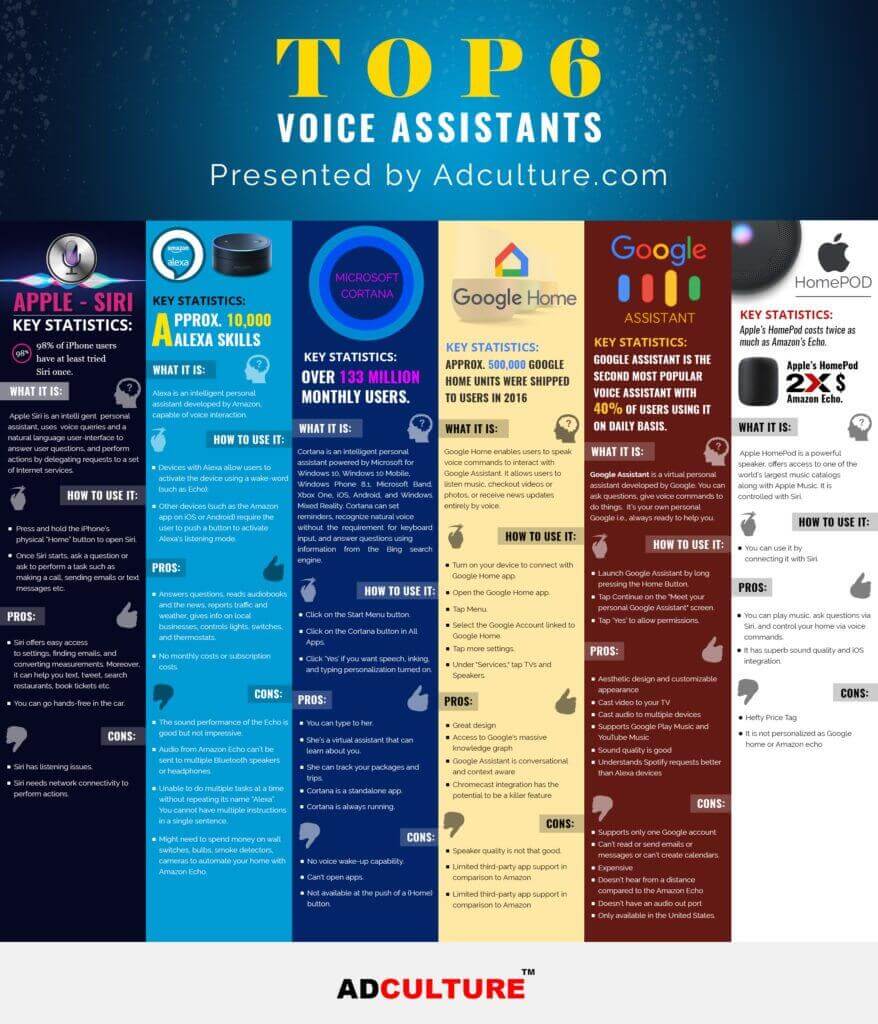
4) Voice Assistants
There are many ways to stay updated on tech tips, from watching helpful YouTube channels to taking advantage of a virtual assistant.
If you haven’t used a voice assistant before, they are essentially little helpers that come with some internet-connect devices; for instance, iPhone users can take advantage of Siri, Apple’s voice assistant. Other popular assistants are Amazon’s Alexa, Microsoft’s Cortana and Google’s Assistant.
Generally, virtual assistants are triggered when you say a keyword.
For example, you say, “OK Google” to access Google’s virtual assistant. After the software is listening, you can say a command or ask a question. One example would be saying, “Alexa, what’s the weather in Salt Lake City?” The personal assistant will then give you a report of the daily weather.
Smart assistants can also help you do other things, like set alarms, turn on smart lights and lock smart doors. As you would imagine, this capability is very helpful when it works perfectly and very scary when it’s not functioning as designed.
According to research conducted at the University of California, Berkeley, many top assistants have vulnerabilities. Hackers can slip secret commands into music on the radio, YouTube videos and other sources of noise to control your smart speakers.
The top hackers use commands that are undetectable to the human ear, so there’s often no way to know when your device is compromised.
Smart programmers start with music and embed speech into the music that’s not recognized as speech by humans. The hard-to-detect speech then instructs the voice assistant to do all sorts of things, such as launching harmful websites.
5) Watches
The benefits of smartwatches seem nearly endless …
Instead of fumbling to find your phone every time it sends you a notification, you can use a watch to see your smartphone’s notifications on your wrist. Additionally, you can reply back to notifications, whether they’re phone calls, text messages or more, directly from your watch.
Smartwatches also set you up for daily success. With smart alarms, you’ll never forget to take a medication or call a loved one on his or her birthday again. Similarly, you never have to be lost, as many of these devices have GPS built directly into them.
These watches can even help you set fitness goals, track your blood pressure, understand your daily calories burned and more. You may even use one of these watches to play music while you exercise.
The myriad of sensors included in a smartwatch allow it to carry out helpful activities, but they’re also a threat to your digital privacy. Since smartwatches store so much data about you, criminals want to hack your armband device to steal your information.
If you use a payment method on your watch, a criminal could even gain access to money in your bank account, apply for a job in your name or claim your tax refund.
Staying Safe
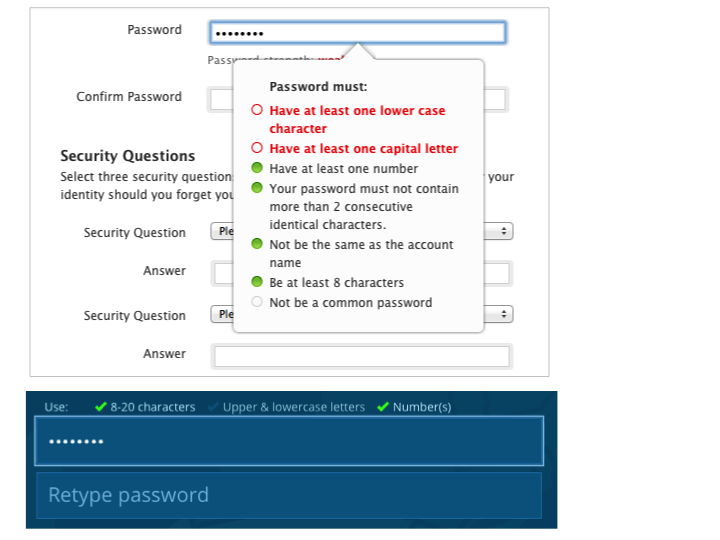
Although there are security risks to using smart devices, there are also ways to increase their safety. First, see if you can add additional safety criteria beyond your personalized password; one example of this is a security question.
In addition, make sure you automatically sign up for security updates, or remember to check for new software monthly, so your devices aren’t as vulnerable.
As you might already know, you never want to run a smart device on public WiFi.
When you’re on an open WiFi network, such as an airport’s WiFi, hackers are more likely to prey on you and try to steal your information. Lastly, as mentioned above, make sure your smart technology is always unused and from a company with a sound track record when it comes to safety.
Do The Benefits Outweigh the Costs?
Now that you understand how to avoid the drawbacks of smart home security, you can choose for yourself and your family what smart devices will enhance your life while limiting your overall exposure and risk.
If you still are unsure of about what popular smart device is right for you, reach out to My Fast PC directly; their computer support representatives can help you understand your current computer problems and talk to you about how technology can improve your life.
That’s right, your first computer diagnosis call is completely free.
Thanks to a costless, remote diagnosis, you can learn if your computer has any complications, whether you know about them or not, and make sure they’re fixed right away for an affordable price.